Security Headers
By default an Axon Ivy Engine will block requests that come from an IFrame of another webserver. It uses the HttpSecurityHeaderFilter as configured in [designerOrEngine]/webapps/ivy/WEB-INF/web.xml (for Ivy 8), or [designerOrEngine]/configuration/web.xml (for Ivy 9+).
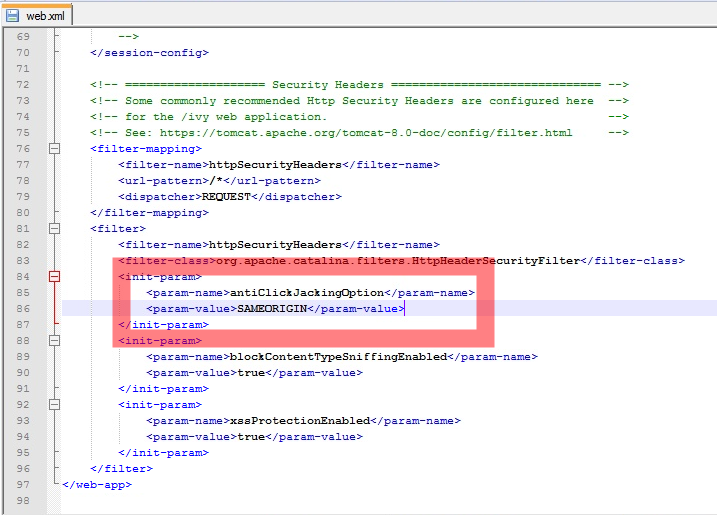
Where to configure security headers
Security headers are usually configured on a front-end web server (reverse proxy) such as Nginx or IIS. The policies are then enforced by the web browser of the client. We recommend setting headers such as the Content-Security-Policy or X-Frame-Options on a front-end web server - not on the Tomcat embedded in Ivy.
However, this tutorial tells you how to deal with these headers if you do not have a front-end webserver.
Allow just single domain access
To enable a specific domain to access Axon Ivy content the init parameters of the HttpSecurityHeaderFilter must be adjusted as follows:
<init-param>
<param-name>antiClickJackingOption</param-name>
<param-value>ALLOW-FROM</param-value>
</init-param>
<init-param>
<param-name>antiClickJackingUri</param-name>
<param-value>http://myRemoteDomainThatEmbeddsAxonIvyWithAnIFrame.com</param-value>
</init-param>
This will set the HTTP response header
X-Frame-Options: ALLOW-FROM http://myRemoteDomainThatEmbeddsAxonIvyWithAnIFrame.com.
Enable the content-security-policy
Unfortunately, the header parameter X-FRAME-OPTIONS is not interpreted by Chrome.
Therefore, access from any Domain is possible when the client uses Chrome.
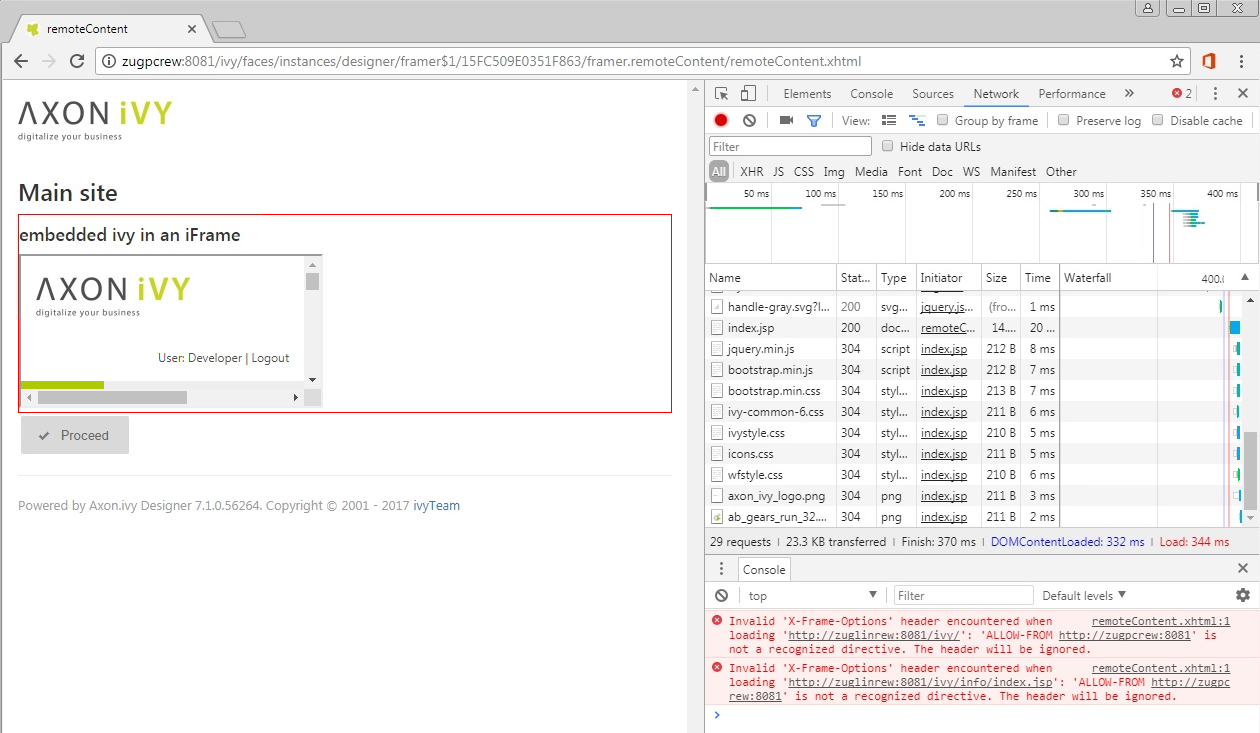
Therefore, you have to set the HTTP response header Content-Security-Policy as well. You can achieve this with a ContentSecurityPolicyFilter. Copy the JAR with this filter into [designerOrEngine]/webapps/ivy/WEB-INF/lib. Then, you can add the filter and configure it in the web.xml.
<filter-mapping>
<filter-name>ContentSecurityPolicyFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>ContentSecurityPolicyFilter</filter-name>
<filter-class>de.saville.csp.ContentSecurityPolicyFilter</filter-class>
<init-param>
<param-name>report-only</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>default-src</param-name>
<param-value>'self' 'unsafe-inline'</param-value>
</init-param>
<init-param>
<param-name>frame-ancestors</param-name>
<param-value>http://myRemoteDomainThatEmbeddsAxonIvyWithAnIFrame.com</param-value>
</init-param>
</filter>
Verify the solution
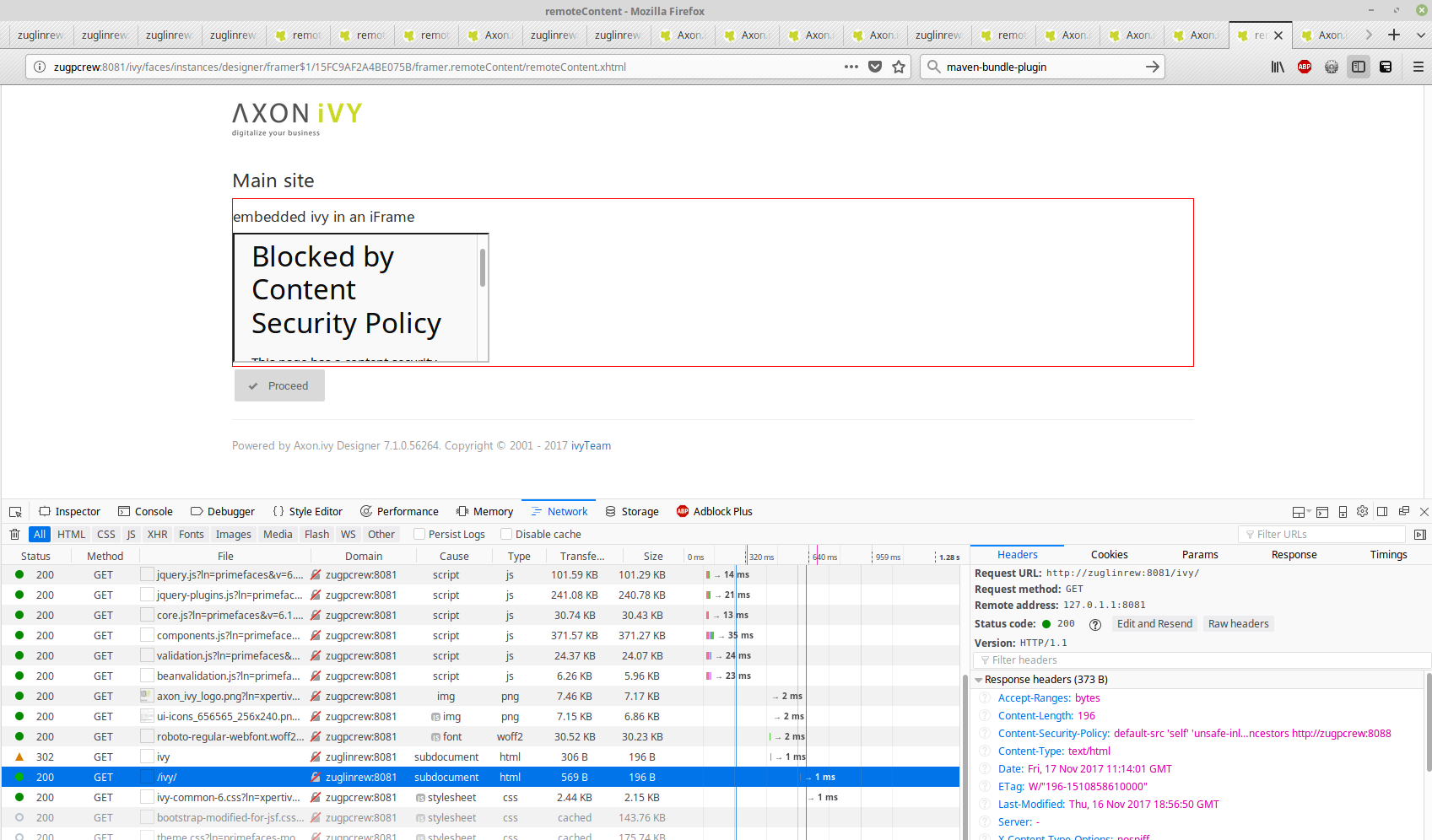
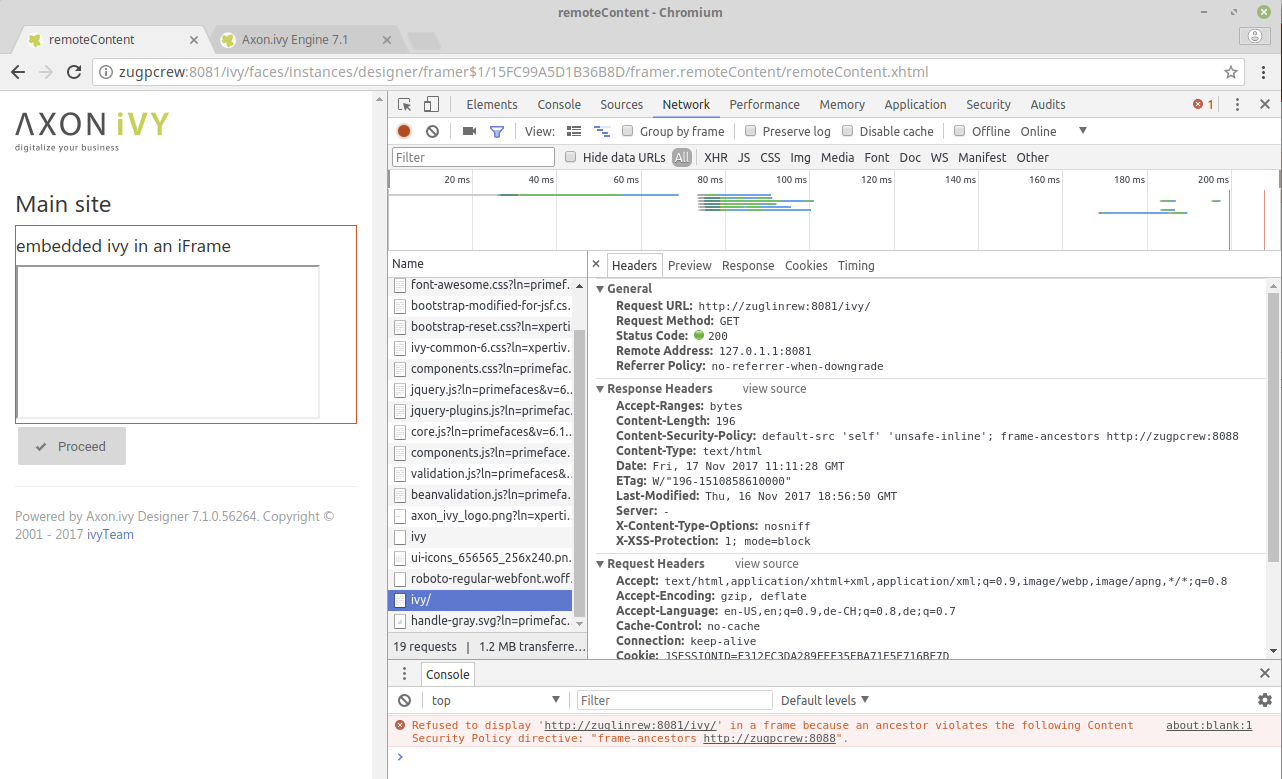
If you try to embed Axon Ivy in an IFrame from a non-whitelisted domain, then you will get an apparent error in the browser console. No content will be visible in the frame. In any request fired against the Axon Ivy Engine, the response header
Content-Disposition-Policy: frame-ancestors https://myParentDomain.com
will be visible.
In Firefox:
In Chrome:
Here is the full web.xml:
<filter-mapping>
<filter-name>httpSecurityHeaders</filter-name>
<url-pattern>/*</url-pattern>
<dispatcher>REQUEST</dispatcher>
</filter-mapping>
<filter>
<filter-name>httpSecurityHeaders</filter-name>
<filter-class>org.apache.catalina.filters.HttpHeaderSecurityFilter</filter-class>
<init-param>
<param-name>antiClickJackingOption</param-name>
<param-value>ALLOW-FROM</param-value>
</init-param>
<init-param>
<param-name>antiClickJackingUri</param-name>
<param-value>http://myremotedomainthatembeddsaxonivywithaniframe.com</param-value>
</init-param>
<init-param>
<param-name>antiClickJackingEnabled</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>blockContentTypeSniffingEnabled</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>xssProtectionEnabled</param-name>
<param-value>true</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>ContentSecurityPolicyFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>ContentSecurityPolicyFilter</filter-name>
<filter-class>de.saville.csp.ContentSecurityPolicyFilter</filter-class>
<init-param>
<param-name>report-only</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>default-src</param-name>
<param-value>'self' 'unsafe-inline'</param-value>
</init-param>
<init-param>
<param-name>frame-ancestors</param-name>
<param-value>http://myremotedomainthatembeddsaxonivywithaniframe.com</param-value>
</init-param>
</filter>